SQL Injection
Version vom 15. Juni 2021, 18:31 Uhr von Thomas.will (Diskussion | Beiträge) (→Verhaltensweise einer SQL Abfrage)
Vorüberlegung
Verhaltensweise einer SQL Abfrage
- Normale Abfrage
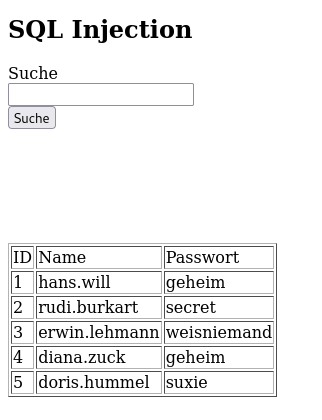
- MariaDB [sql_injections]> select * from users where username = 'rudi.burkart';
+------+--------------+----------+ | id | username | password | +------+--------------+----------+ | 2 | rudi.burkart | secret | +------+--------------+----------+ 1 row in set (0.000 sec)
- Oder Verknüpfung
- MariaDB [sql_injections]> select * from users where username = 'rudi.burkart' or username = 'hans.will';
+------+--------------+----------+ | id | username | password | +------+--------------+----------+ | 2 | rudi.burkart | secret | | 1 | hans.will | geheim | +------+--------------+----------+ 2 rows in set (0.000 sec)
PHP Code
Unsicher
<?php
error_reporting(E_ERROR | E_PARSE);
if(isset($_POST['submit'])){
define('DB_SERVER', 'db');
define('DB_USERNAME', 'xinux');
define('DB_PASSWORD', 'suxer');
define('DB_NAME', 'sql_injections');
$link = mysqli_connect(DB_SERVER, DB_USERNAME, DB_PASSWORD, DB_NAME);
mysqli_set_charset($link, "utf8");
if($link === false){
echo(mysqli_connect_error());
die("ERROR: Could not connect. " . mysqli_connect_error());
}
//connect db
include "inc/connect.php";
//safe query
$search = mysqli_real_escape_string($link, $_POST['search']);
//Database search
$sql = "SELECT * FROM users WHERE username='$search'";
$result = mysqli_query($link, $sql);
}
?>
<!DOCTYPE html>
<html>